The basis for automating tasks is choosing a programming language that will help us achieve our goal. I chose Python because it is available both on Windows and Linux and is used as the basic language in SOAR (Security Orchestration, Automation, and Response) applications. This language is high-level, and, with the use of available libraries, it has unlimited possibilities. In this article, I will present the first steps of task automation, and introduce and demonstrate the use of Splunk SOAR as an example.
First steps of task automation
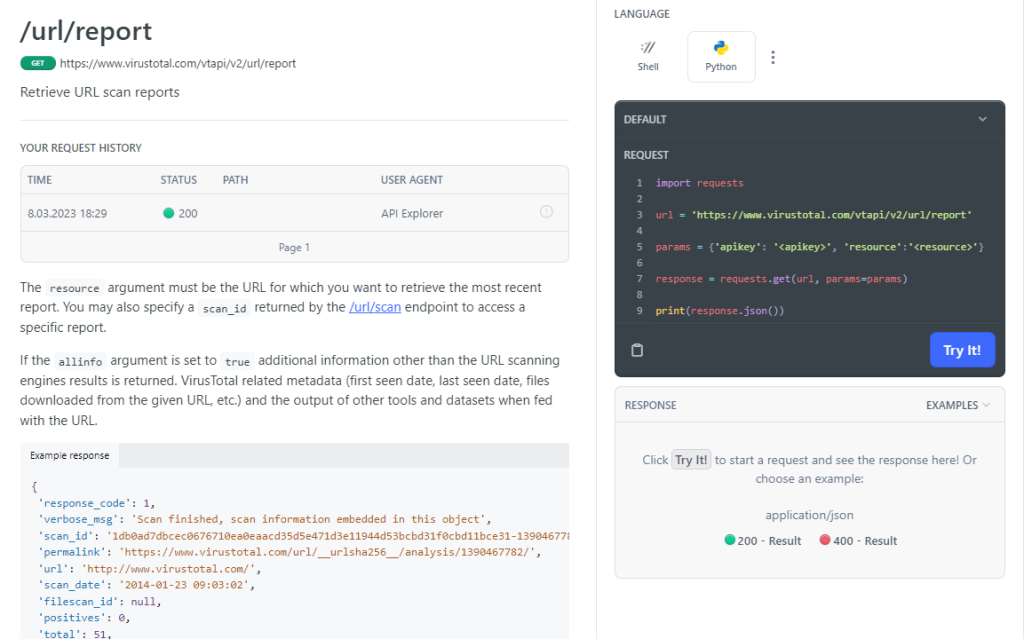
My experience with task automation started with learning the basics of programming this language and setting a goal for myself – in my case, it was checking multiple IOC (Indicator of Compromise) URLs on VirusTotal.com. On the VT website, you can find very good documentation for the API (Application Programming Interface) that can help you create a connection, authenticate, send and receive requests. Sometimes, as in this case, an almost complete solution is given in the documentation:
All you need to do is search for the action you need, change the language from the default Shell to Python and fill in the fields as in the url and x-apikey example. In the documentation, we also have help in the form of required libraries and how to install them in our environment.
For my purpose, it was enough to copy the program code and slightly modify it to be able to scan 100 URLs at a time, instead of manually clicking through WebGui or changing the URL parameter in the program code.
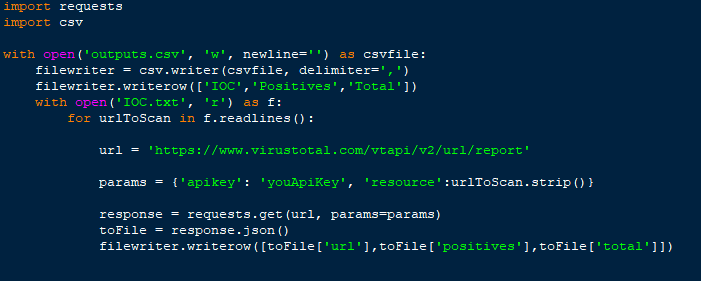
Fortunately, I had the IOC file available, so I simply imported it into the program and made connections to the service in a loop, and saved the results to a separate file. The response from the server contains a lot of information but for me, the most important were the URL, the number of positive results, and the sum of all scans.
For example, the program code in Python:
As you can see, a simple code modification saved a few hours of checking a 100 URLs on the website. Many of today’s leading services have an API to automate or not graphically connect to it and get the same data or even more.
Using Splunk SOAR
A similar solution to the topic and a broader use of task automation is provided, for example, by Splunk SOAR (formerly Phantom). It is a great tool from the Splunk family that works perfectly with Splunk Enterprise Security and the notable events (incidents of very high-severity) generated there.
All limitations of Splunk ES can be solved with the help of Splunk SOAR and its Playbooks and the resulting automation. What cannot be done with the available actions from the application can be freely programmed using the Python language in existing blocks, which is not recommended, or in Custom Functions dedicated for this purpose.
In a well-configured Splunk SOAR environment with appropriate applications and Playbooks, you can, for example:
- verify reported emails as Phishing,
- automatically extract all available IOCs – visible and hidden in the email code and attachments,
- verify the validity of the user who reported the email,
- automatically expand short URLs and extract domains and IPs from domains and URLs,
- check if a given email address, subject, or content is not on the White List,
- check the reputation of acquired IOCs on various external or internal services,
- send e-mails to Sandbox automatically,
- upload e-mails to AI,
- automatically verify parameters from Header, such as dmarc, dkim, spf,
- check in the local or external database if the sender is not on the Black List,
- check previously reported emails for similarities and close automatically if a similar message is found,
- block the sender’s URL, clear mailboxes from other users’ reported emails,
- or many other actions that the analyst must perform manually in various services and it could be done automatically using applications using API to perform tasks
Example of Splunk SOAR usage
Splunk SOAR can also be used for scanning 100 URLs, described as an example at the beginning of the article.
For this purpose, it is best to create a new Playbook. Then, just add a block with the Virustotal application, in which we select the “url reputation” action, and in the url field select artifact.requestUrl. Then we save the Playbook with any name and choose to work on all labels.
For example, we go to source -> events and create a new container, into which we put the IOC.txt file in the Files tab. Then we run the action button and select the “extract ioc” action from the Parser application, which will extract all URLs from the IOC.txt file. We enter the vaultId of the previously saved file and run the action. This will create 100 artifacts that will be used for the previously created Playbook.
Then we run our Playbook and it will create a series of queries to VirusTotal. Thanks to this, we easily get information about the reputation of each URL from the file. The result of the application can be found in the Widgets tab at the bottom of the page.
As you can easily see, the automation of tasks with Splunk SOAR does not require knowledge of programming, only simple skills in using this application. However, not everyone will be satisfied with the result of this operation.
The next step should be to customize the results to the needs, i.e. enter the most important information directly into the artifact. To do this, use the Custom function block and the update_artifact command to update the artifact with the positives, a total result for each artifact. In addition, you can also change the serverity from the default medium to low or high depending on the number of positives found by VirusTotal. Thanks to this, we will get a clear view of the artifacts containing the URL with the results we are interested in. The obtained results can also be exported to a file in JSON format and used in other systems.
The given Playbook is only an example of using the VirusTotal application, however, nothing prevents us from easily adding additional reputation-checking services and logic that unifies the results and provides simple scoring for the analyst.
Summary
In the analysis of Cybersecurity incidents, there is less and less room for manual analysis at the moment. Thanks to the use of automation in as many places as possible, we can afford to obtain more standardized results from many different sources. This allows us to shift the available human resources to more demanding security incidents and to provide additional knowledge training for analysts.
***
If you are interested in the Cybersecurity area, we also recommend other articles written by our experts
















Leave a comment