Security in embedded systems — just an option or already a must?
Recently, the importance of security in the world of technology has surged. For most of us, it’s a tangible means of preventing failures, logical errors, and other problems that may crop up when using modern devices. There’s a belief in the market that this issue primarily pertains to the IoT (Internet of Things) devices, with the solution itself often considered optional. Many companies designing embedded systems focus solely on securing the installed software from unauthorized access or copying. Other problems related to safeguarding collected data, calibration data, and configuration data are sometimes ignored. Nonetheless, it’s crucial to remember that nowadays, systems are becoming increasingly interconnected, exchanging larger volumes of data and mutually influencing the decision-making process regarding control. But is such an approach the right one? Find out how Marek Natunewicz, Solution Architect at Sii Poland and a specialist at the Embedded Competency Center, comments on it in a self-authored material.
Cyber threats: it used to be safer
With the advancement of technology in the embedded systems market, we’re witnessing a disturbing rise in cybercrime, ranging from industrial espionage to hacking attacks and system breaches. The “ENISA Threat Landscape 2023” report reveals a significant uptick in incidents compared to previous years. According to Forbes magazine, global cyberattack costs surpassed USD 10.5 trillion in 2023.
Embedded systems streamlining our daily tasks play an increasingly important role in our lives. Their use entails generating vast amounts of data, including calculation results, settings, access credentials, source codes, or behavior patterns. There is a risk that this data could fall into the wrong hands through hacking, leading to misuse or complete control over the system.
(Un)safe devices?
Users often believe their devices are secure because they don’t gather information that could be valuable to potential intruders. This especially applies to products installed in hard-to-reach places or not connected to other devices. But that couldn’t be further from the truth. Cybercriminals can gain unauthorized access to individual devices and complex systems through various transmission ports, screens, keyboards, signaling elements, and radio communication components.
Even seemingly simple devices like garage door openers or lighting controls collect data such as opening and closing times or when someone is at home. Though seemingly trivial, this information can be a valuable source of knowledge for those intending to exploit it. That’s why implementing security measures is crucial, even for straightforward systems.
Security guide
Uncertainty among companies adopting security protocols for embedded systems often arises from unfamiliarity with norms, standards, and legal regulations or a lack of comprehension. Regardless of the nature of the implementing company’s activities and the sector in which it operates, the first step should always involve familiarizing themselves with the relevant guidelines.
Standards regarding security principles
There are dozens of standards concerning security principles that need to be implemented in electronic devices. The main purpose of these standards is to describe the processes related to the design, implementation, maintenance, management, and monitoring of threats and vulnerabilities, with an emphasis on security. In addition to providing general guidance, these standards are intended to serve as sources of best practices for ensuring the highest level of protection.
The graphic below lists the most important standards for embedded devices across different sectors. Some standards focus on IoT systems, others cover the entire system, while the rest describe security-related topics more generally.
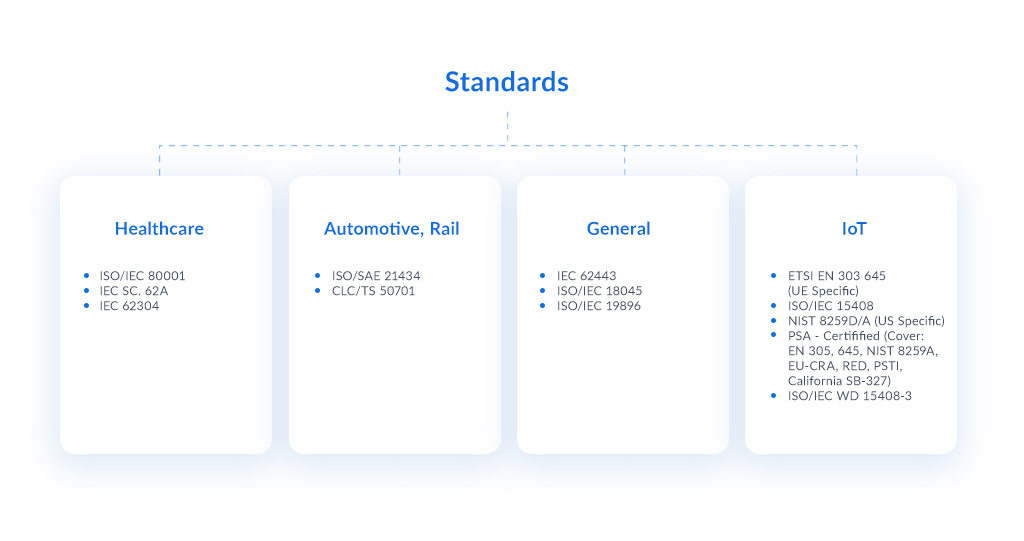
Image 1. Popular norms and standards regarding security.
Often, companies struggle to choose a standard that fits their device. Consequently, they try to develop security procedures on their own, drawing from suitable elements of various available standards. — Incorrect analysis due to insufficient knowledge and rushing can significantly hinder, and in the worst-case scenario, even prevent the effective implementation of required norms – says Monika Jaworowska, Embedded Competency Center Director at Sii Polska. — Therefore, it’s worth seeking help from experienced specialists in embedded systems security, whose expertise will enable understanding and applying the right standards tailored to specific industry requirements and processes — she adds.
Regulations regarding security principles
Intensive efforts have been made in the European Union, the United States, and the United Kingdom to implement new legal regulations regarding security principles. Some are already in effect, while others are still in the works. The EU has also adopted a security strategy largely based on existing norms and standards.
In 2025, the EU-RED directive will be introduced, covering electronic devices equipped with wireless communication features such as Bluetooth, WiFi, or Zigbee. Then, in 2027, the EU-CRA directive will come into effect, requiring the application and implementation of security principles in all electronic devices with a digital control unit. In the United Kingdom, obligations regulated by UK-PSTI will be imposed within a year.
Most of the implemented regulations include or will include a transitional period lasting from several months to several years, allowing companies to adapt their products to the new legal regulations. However, the suggested timeframe is very short compared to the scope of work to be done, so it’s advisable to start implementation as soon as possible.
When is the implementation of security principles necessary?
Given the rapid advancement of embedded systems, it’s no longer sufficient to simply design devices that only fulfill a predetermined scope of logic. Security awareness is on the rise, prompting customers to meticulously assess whether a product meets standards and norms before making a purchase decision.
Many companies believe they can address device security post-preparation for production and sale. Unfortunately, that’s not the case. Security should be seamlessly integrated throughout the entire tool development process and should not be neglected at any stage. Security principles must be incorporated into the final product from the design phase. This entails conducting risk and vulnerability analyses and identifying all elements and data that could be targeted in attacks. Moreover, it’s advisable to incorporate “secure coding” practices and design software with potential threats in mind.
Of course, there’s the option to implement security principles at a later stage. However, this comes with added expenses, extended timelines, and system redesign. On the other hand, taking action right from the project’s outset yields significant benefits regarding both efficiency and costs.

Image 2. Pros and cons of implementing security principles
Investing in quality and company reputation
Security in embedded systems isn’t an easy topic. Given the alarming surge and scale of cybercrime, mitigating threats is no longer a choice but an absolute must. By implementing security principles, companies protect sensitive data from unauthorized access, minimize the risk of failures, attacks, and errors, and ensure user safety and comfort. This, in turn, fosters trust and loyalty among customers.
Want to learn more about embedded systems security? Contact the experts at Sii Polska.













